RDP-соединения не работают при определенных обстоятельствах
проблема
Соединения RDP от ПК или серверов в обоих филиалах к серверу RDSH в главном сайте периодически прерываются со следующей ошибкой:
A licensing error occurred while the client was attempting to connect (Licensing timed out).
Please try connecting to the remote computer again.
конфигурация
Основной сайт использует ZyXEL ZyWALL USG 50, ему назначена подсеть 192.168.169.0/24 и размещен сервер RDSH 192.168.169.4.
Сайт филиала, который я использовал для диагностики, использует Cyberoam CR10iNG, ему назначена подсеть 192.168.170.0/24 и размещен сервер 192.168.170.2.
Все сайты подключены через VPN-соединения IPsec.
Значения MTU всех интерфейсов UTM для интерфейсов LAN и WAN равны 1500 (это актуально позже).
диагностика
Мне удалось определить два шаблона для этого:
- Проблема возникает только при попытке подключения через ~2 минуты после предыдущей попытки подключения / проблема не возникает при попытке подключения через ~1 минуту после предыдущей попытки подключения.
- Проблема возникает только после этапа аутентификации.
UTM сайта филиала захватывает входящие и исходящие пакеты при возникновении проблемы:
console> tcpdump ' host 192.168.170.2 and host 192.168.169.4
tcpdump: Starting Packet Dump
15:01:53.093210 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [S], seq 2596326655, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
15:01:53.093838 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [S], seq 2596326655, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
15:01:53.123625 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [S.], seq 2739636351, ack 2596326656, win 8192, options [mss 1394,nop,wscale 8,nop,nop,sackOK], length 0
15:01:53.123914 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [S.], seq 2739636351, ack 2596326656, win 8192, options [mss 1394,nop,wscale 8,nop,nop,sackOK], length 0
15:01:53.124049 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 1, win 261, length 0
15:01:53.124205 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 1, win 261, length 0
15:01:53.124297 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 1, win 261, length 19
15:01:53.124498 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 1, win 261, length 19
15:01:53.161897 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 20, win 514, length 0
15:01:53.161911 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 20, win 514, length 19
15:01:53.162228 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 20, win 514, length 0
15:01:53.162235 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 20, win 514, length 19
15:01:53.365124 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 20, win 261, length 0
15:01:53.365350 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 20, win 261, length 0
15:01:56.169042 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 20, win 514, length 19
15:01:56.169354 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 20, win 514, length 19
15:01:56.169497 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 20, win 261, options [nop,nop,sack 1 {1:20}], length 0
15:01:56.169717 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 20, win 261, options [nop,nop,sack 1 {1:20}], length 0
15:01:58.770755 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 20, win 261, length 141
15:01:58.771026 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 20, win 261, length 141
15:01:58.810913 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 161, win 514, length 1209
15:01:58.811110 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 161, win 514, length 1209
15:01:58.838206 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 1229, win 256, length 134
15:01:58.838396 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 1229, win 256, length 134
15:01:58.870753 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 295, win 513, length 59
15:01:58.870943 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 295, win 513, length 59
15:01:58.871956 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 1288, win 256, length 197
15:01:58.872149 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 1288, win 256, length 197
15:01:58.901929 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 492, win 512, length 1237
15:01:58.901944 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 492, win 512, length 1237
15:01:58.905117 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 2525, win 261, length 1394
15:01:58.905130 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [.], ack 2525, win 261, length 1394
15:01:58.905271 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 2525, win 261, length 339
15:01:58.905286 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 2525, win 261, length 339
15:01:58.935194 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 2225, win 506, length 0
15:01:58.935208 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 2225, win 506, length 0
15:01:58.935211 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 2225, win 512, length 0
15:01:58.935225 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 2225, win 512, length 0
15:01:58.935663 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 2225, win 512, length 261
15:01:58.935675 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 2225, win 512, length 261
15:01:58.936427 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 2786, win 260, length 437
15:01:58.936441 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 2786, win 260, length 437
15:01:58.965251 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 2662, win 510, length 373
15:01:58.965265 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 2662, win 510, length 373
15:01:58.966104 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3159, win 258, length 197
15:01:58.966117 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3159, win 258, length 197
15:01:58.966183 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3159, win 258, length 469
15:01:58.966198 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3159, win 258, length 469
15:01:59.009189 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 3328, win 507, length 0
15:01:59.009203 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 3328, win 507, length 0
15:01:59.009206 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 3328, win 514, length 0
15:01:59.009219 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 3328, win 514, length 0
15:01:59.009403 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3328, win 514, length 149
15:01:59.009415 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3328, win 514, length 149
15:01:59.009822 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3308, win 258, length 53
15:01:59.009840 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3308, win 258, length 53
15:01:59.009889 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3308, win 258, length 37
15:01:59.009900 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3308, win 258, length 37
15:01:59.038280 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 3418, win 514, length 0
15:01:59.038294 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [.], ack 3418, win 514, length 0
15:01:59.038521 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3418, win 514, length 37
15:01:59.038535 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3418, win 514, length 37
15:01:59.038936 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3345, win 258, length 53
15:01:59.038949 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3345, win 258, length 53
15:01:59.074195 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3471, win 514, length 53
15:01:59.074209 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3471, win 514, length 53
15:01:59.074601 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3398, win 257, length 53
15:01:59.074614 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3398, win 257, length 53
15:01:59.101963 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3524, win 514, length 53
15:01:59.101976 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3524, win 514, length 53
15:01:59.102388 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3451, win 257, length 53
15:01:59.102402 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3451, win 257, length 53
15:01:59.131316 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3577, win 513, length 53
15:01:59.131330 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3577, win 513, length 53
15:01:59.131741 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3504, win 257, length 53
15:01:59.131755 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3504, win 257, length 53
15:01:59.163405 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3630, win 513, length 53
15:01:59.163418 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3630, win 513, length 53
15:01:59.163838 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3557, win 257, length 53
15:01:59.163851 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3557, win 257, length 53
15:01:59.190262 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3683, win 513, length 53
15:01:59.190275 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3683, win 513, length 53
15:01:59.190680 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3610, win 257, length 53
15:01:59.190694 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3610, win 257, length 53
15:01:59.217563 ipsec0, IN: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3736, win 513, length 53
15:01:59.217577 PortA, OUT: IP 192.168.169.4.3389 > 192.168.170.2.58969: Flags [P.], ack 3736, win 513, length 53
15:01:59.302857 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:01:59.302869 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:01:59.589676 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:01:59.589689 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:00.198617 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:00.198631 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:01.399393 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:01.399409 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:02.600639 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:02.600653 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:03.802102 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:03.802115 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:06.204902 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:06.204918 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:11.009880 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:11.009895 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [P.], ack 3663, win 256, length 437
15:02:20.619699 PortA, IN: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [R.], seq 4173, ack 3663, win 0, length 0
15:02:20.619715 ipsec0, OUT: IP 192.168.170.2.58969 > 192.168.169.4.3389: Flags [R.], seq 4173, ack 3663, win 0, length 0
^C
104 packets captured
104 packets received by filter
0 packets dropped by kernel
console>
Перехват входящего пакета UTM основного сайта при возникновении проблемы:
Router> packet-trace interface lan1 src-host 192.168.170.2 dst-host 192.168.169.4
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth2, link-type EN10MB (Ethernet), capture size 68 bytes
13:35:03.378214 IP 192.168.170.2.58969 > 192.168.169.4.3389: S 2596326655:2596326655(0) win 8192 <mss 1402,nop,wscale 8,nop,nop,sackOK>
13:35:03.409321 IP 192.168.170.2.58969 > 192.168.169.4.3389: . ack 2739636352 win 261
13:35:03.409488 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 0:19(19) ack 1 win 261
13:35:06.454025 IP 192.168.170.2.58969 > 192.168.169.4.3389: . ack 20 win 261 <nop,nop,sack sack 1 {1:20} >
13:35:09.054995 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 19:160(141) ack 20 win 261
13:35:09.123072 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 160:294(134) ack 1229 win 256
13:35:09.156294 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 294:491(197) ack 1288 win 256
13:35:09.189996 IP 192.168.170.2.58969 > 192.168.169.4.3389: . 491:1885(1394) ack 2525 win 261
13:35:09.190141 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 1885:2224(339) ack 2525 win 261
13:35:09.220727 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 2224:2661(437) ack 2786 win 260
13:35:09.264170 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 2661:2858(197) ack 3159 win 258
13:35:09.264313 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 2858:3327(469) ack 3159 win 258
13:35:09.293790 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3327:3380(53) ack 3308 win 258
13:35:09.293933 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3380:3417(37) ack 3308 win 258
13:35:09.322616 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3417:3470(53) ack 3345 win 258
13:35:09.358341 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3470:3523(53) ack 3398 win 257
13:35:09.387431 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3523:3576(53) ack 3451 win 257
13:35:09.415444 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3576:3629(53) ack 3504 win 257
13:35:09.447532 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3629:3682(53) ack 3557 win 257
13:35:09.474161 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3682:3735(53) ack 3610 win 257
13:35:09.586635 IP 192.168.170.2.58969 > 192.168.169.4.3389: P 3735:4172(437) ack 3663 win 256
13:35:09.596816 IP 192.168.170.2 > 192.168.169.4: icmp: 192.168.170.2 unreachable - need to frag (mtu 1434)
^C
22 packets captured
44 packets received by filter
0 packets dropped by kernel
Router>
Захват исходящего пакета UTM основного сайта при возникновении проблемы:
Router> packet-trace interface lan1 src-host 192.168.169.4 dst-host 192.168.170.2
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth2, link-type EN10MB (Ethernet), capture size 68 bytes
13:35:03.379281 IP 192.168.169.4.3389 > 192.168.170.2.58969: S 2739636351:2739636351(0) ack 2596326656 win 8192 <mss 1460,nop,wscale 8,nop,nop,sackOK>
13:35:03.419429 IP 192.168.169.4.3389 > 192.168.170.2.58969: . ack 20 win 514
13:35:03.419439 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 1:20(19) ack 20 win 514
13:35:06.427459 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 1:20(19) ack 20 win 514
13:35:09.067035 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 20:1229(1209) ack 161 win 514
13:35:09.128270 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 1229:1288(59) ack 295 win 513
13:35:09.158237 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 1288:2525(1237) ack 492 win 512
13:35:09.192298 IP 192.168.169.4.3389 > 192.168.170.2.58969: . ack 2225 win 506
13:35:09.192309 IP 192.168.169.4.3389 > 192.168.170.2.58969: . ack 2225 win 512
13:35:09.192312 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 2525:2786(261) ack 2225 win 512
13:35:09.222233 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 2786:3159(373) ack 2662 win 510
13:35:09.266517 IP 192.168.169.4.3389 > 192.168.170.2.58969: . ack 3328 win 507
13:35:09.266527 IP 192.168.169.4.3389 > 192.168.170.2.58969: . ack 3328 win 514
13:35:09.266530 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3159:3308(149) ack 3328 win 514
13:35:09.295276 IP 192.168.169.4.3389 > 192.168.170.2.58969: . ack 3418 win 514
13:35:09.295286 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3308:3345(37) ack 3418 win 514
13:35:09.331527 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3345:3398(53) ack 3471 win 514
13:35:09.359430 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3398:3451(53) ack 3524 win 514
13:35:09.388479 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3451:3504(53) ack 3577 win 513
13:35:09.420695 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3504:3557(53) ack 3630 win 513
13:35:09.448129 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3557:3610(53) ack 3683 win 513
13:35:09.475201 IP 192.168.169.4.3389 > 192.168.170.2.58969: P 3610:3663(53) ack 3736 win 513
13:35:09.592050 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:5065(1402) ack 4173 win 511
13:35:09.592061 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 5065:6467(1402) ack 4173 win 511
13:35:09.592064 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 6467:7869(1402) ack 4173 win 511
13:35:09.897681 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:5057(1394) ack 4173 win 517
13:35:10.506021 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:5057(1394) ack 4173 win 517
13:35:11.706834 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:4199(536) ack 4173 win 517
13:35:12.907933 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:4199(536) ack 4173 win 517
13:35:14.105571 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:5057(1394) ack 4173 win 517
13:35:16.510943 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:5057(1394) ack 4173 win 517
13:35:21.335328 IP 192.168.169.4.3389 > 192.168.170.2.58969: . 3663:5057(1394) ack 4173 win 517
13:35:30.935793 IP 192.168.169.4.3389 > 192.168.170.2.58969: R 5057:5057(0) ack 4173 win 0
^C
33 packets captured
66 packets received by filter
0 packets dropped by kernel
Router>
13:35:09.596816 IP 192.168.170.2 > 192.168.169.4: icmp: 192.168.170.2 unreachable - need to frag (mtu 1434) кажется ключом.
Сбой проверки связи с сайта филиала на сервере RDSH с набором "Не фрагментировать" на 1473 B: 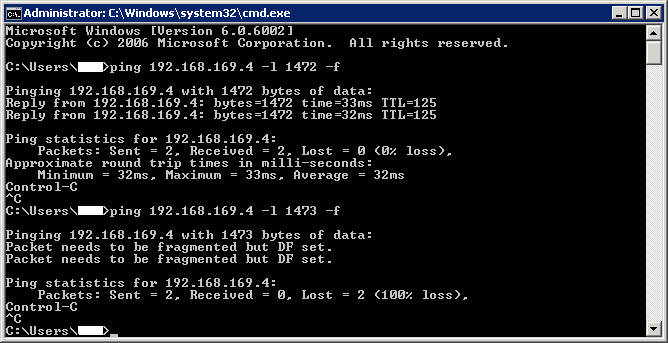
Соединения RDP от и к тем же хостам, но через общий Интернет / не через IPsec VPN кажутся незатронутыми.
1 ответ
Переконфигурирование ZyXEL ZyWALL USG 50 на главном сайте с включенной опцией Ignore "Don't Fragment" setting in IP header решил вопросы.